- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
Energy & Utilities Sector
Cyber Security
Cyber Security
Identify, Protect, Detect, Respond & Report on Healthcare Data Breaches
Request demoStaffCop for the Energy & Utilities Sector
In the past, the energy and utilities industry was mainly plagued by threats from external actors - a challenge it addressed by adopting better security measures. Now, it is difficult for outsider attackers to penetrate critical energy and utilities systems.
Unfortunately, these criminals are adapting and have found a new way to carry out their attacks – they now recruit insiders, employees and contractors in these organizations to gain access. These insider attacks cost the energy industry tens of millions on average.
What’s more, large utilities often utilize contractors, outsourcing partners and suppliers for offshore operations, exploration, distribution, analysis and legal matters. These third-parties can easily expose the company to great financial, IP and other risks either accidentally or intentionally.
In an industry where employees, vendors, and contractors have access to critical infrastructures and sensitive data on a regular basis, securing the resources and information is crucial for the industry as well as for the safety of the citizens utilizing their products and services.
StaffCop Combines Insider Threat Detection and Data Loss Prevention into a Single Integrated Solution for Energy & Utilities Companies
With StaffCop, energy and utility companies can monitor and protect critical infrastructure from malicious or accidental insider threats and meet compliance goals for NERC, FISMA, ISO 27001 with its powerful policy and rules engine, forensic audit, and reporting features.
Offers operation-wide visibility into the user activity of critical infrastructure assets for both OT and IT systems.
Prevents stealing of high value intellectual property like survey and testing data, drilling and logistics and so on.
Extends monitoring and control to all third-parties for secure collaboration on joint-venture projects.
Limits the modification of system software, access elevation and other potential harmful activity by privileged users.
Defend customer information, employee privacy and corporate data.
1
Monitor Critical Systems and Users
StaffCop monitors all user activity over IT and OT systems and cloud for 22+ system objects.
2
Detect Insider Threats
StaffCop detects malicious activities and anomalies and takes immediate actions like warn, lockout user or take remote control of a system when rule violation is detected.
3
Discover & Categorize Sensitive Data Automatically
Deep content inspection in both structured and unstructured data accurately and identifies classified and confidential information.
4
Safeguard Data and IP
StaffCop protects confidential design, production and exploration plans, IP and other sensitive information from falling into the wrong hands.
5
Enable Secure Collaboration
Leverages a combination of terminal servers, VMWare or Citrix servers to allow collaboration with partners in a secure sandbox.
6
Conduct Cybersecurity Risk Assessment
With StaffCop’s dynamic risk scoring and vulnerabilities scanning ability, companies can identify at risk employees, policies, and system resources.
7
Coordinate Security Orchestration for Rapid Response
By utilizing StaffCop, you can create a cybersecurity perimeter across your stores, supply chain network and corporate offices and much more.
8
Protect Your Operations from 3rd-Party Threats
Monitor all third party entities who have access to your critical systems to prevent sabotage or data theft.
9
Investigate Incidents with Forensics and Audit
Enforce training and awareness programs with Session Recording & Playback and customized rule violation messages.
Industry Statistics Show the Need for Privileged User Activity Monitoring
Security is top priority for utilities
Cyber and physical security were the most pressing concerns for utility companies, says UtilityDive.
72% Agree Cyber & Physical Security is imperative
Energy is one of the most targeted critical sectors
According to a report by DHS, the U.S. energy sector, is one of the most highly targeted critical infrastructure sectors.
59% Cyber Incidents are Related to U.S. Energy Sector
Insiders are the biggest security threat in the oil and gas industry
In a Ponemon & Symantec survey, 65% of OT experts identified careless insiders as the top cybersecurity threat, while 15% said malicious insiders.
65% Negligent Insider
15% Malicious Insider
Insider threats cost energy and utilities companies millions
Utilities incurred an average cost of $10.23 million due to insider threat related incidents in 2018, according to Ponemon & ObserveIT.
$10M+ Cost of Insider Threats for Energy & Utilities Companies
StaffCop Helps Energy and Utilities Companies Protect Confidential Data
Energy
– Exploration, seismic, survey and other research data.
– Process flow, pipeline flow diagram, engineering designs.
– Oil/gas drilling data like prospecting related terms, confidential/CB well list, Coalbed data etc.
– Business plans, legal data.
– Process flow, pipeline flow diagram, engineering designs.
– Oil/gas drilling data like prospecting related terms, confidential/CB well list, Coalbed data etc.
– Business plans, legal data.
Critical infrastructure / utilities
– Software design documents, SCADA terms, distribution plans
– Vendor Contracts.
– Business plans, legal data.
– Customer Data, Personally identifiable information (PII), Customer proprietary network information (CPNI).
– Vendor Contracts.
– Business plans, legal data.
– Customer Data, Personally identifiable information (PII), Customer proprietary network information (CPNI).
Corporate data
– Strategic plans and business processes.
– Price/cost/supplier/customer lists.
– Source code, formulas, and other type of IPs.
- Consumer-specific Energy Usage Data (CEUD).
- Acquisition plans, M&A announcements, legal documents and other sensitive matters.
– Payroll, accounting and financial data.
– Price/cost/supplier/customer lists.
– Source code, formulas, and other type of IPs.
- Consumer-specific Energy Usage Data (CEUD).
- Acquisition plans, M&A announcements, legal documents and other sensitive matters.
– Payroll, accounting and financial data.
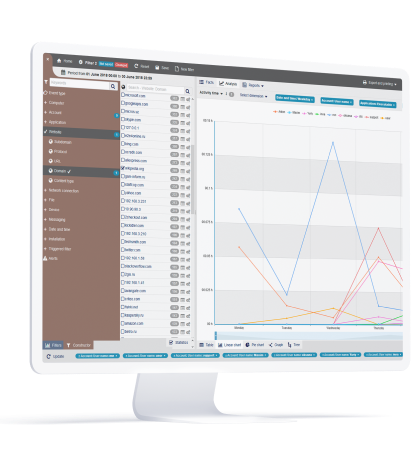
Real-Time Visibility and Control
StaffCop visually records every action that a user makes on your OT and IT systems and cloud, DMZ for 22+ system objects. Each object can be programmed to take into consideration what needs to be monitored and who has access to the monitored records. You can specify who you want to monitor, how much you want to monitor, when and for how long.
Automated Data Discovery and Classification
StaffCop has built-in templates for many classified and unclassified data types to protect your customer data, IP and other sensitive information.

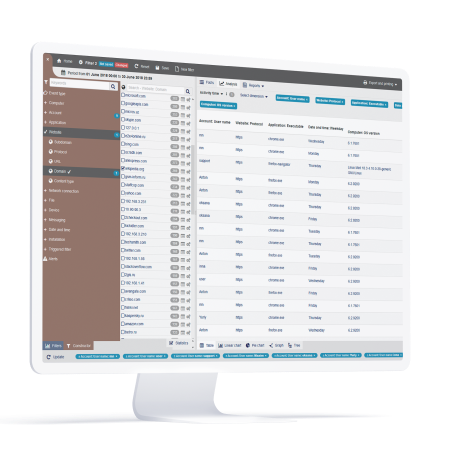
Powerful Policies and Rules Engine
The core of the StaffCop platform is its automation. StaffCop comes with hundreds of pre-defined policies and rules. For example: block email containing sensitive keywords, stop uploading of a confidential document, detect screen capture, prevent the use of external drives etc. The templates cover virtually every use case of data loss prevention, insider threat detection and compliance requirements. Just pick a policy or rule template and all the data definition, content source, condition will be set automatically for you to edit.
Endpoint Data Loss Prevention & Egress Control
StaffCop’s exfiltration and egress controls allow you to monitor and prevent illicit sharing of information. For instance, File Transfer rules to prevent the use of removable media.
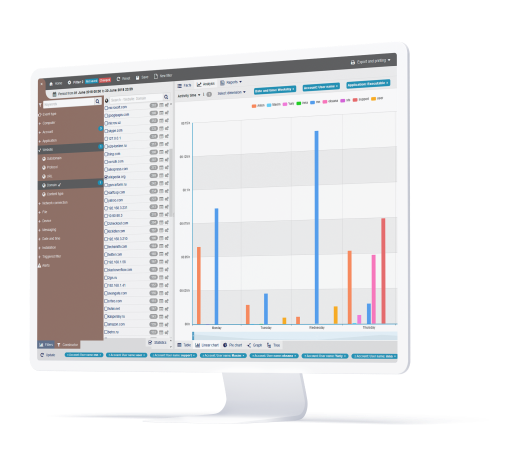
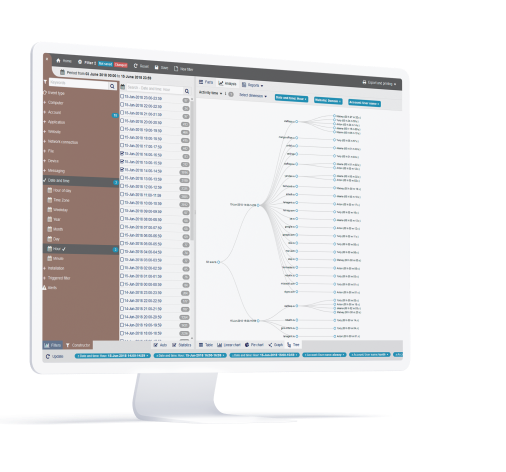
Behavioral Anomaly Detection
StaffCop allows you to define what constitutes dangerous user behavior, then uses its sophisticated anomaly engine to automatically detect when a user, department, or group deviates from their normal parameters or exceeds acceptable risk levels. Once a threat is detected, it notifies appropriate authorities, locks out the user or takes remote control of the compromised system.
Privileged User and Third-Party Monitoring
StaffCop allows organizations to create profiles for employees and third parties and define what information and system resources each profile can access. Further rules can be established by behavior policies so that access to sensitive information is segregated by the organization’s security policy, or on a need-to-know basis.

Digital Forensics and Auditing
Detailed alerts including any security incidents and what actions were taken can be viewed. Warning messages can be programmed to inform the users about nonconformity and influence corrective behavior. Session recordings and history playback can be leveraged to view user’s desktop for audit and evidence gathering purposes
Risk Assessment and Treatment
CSO and security analysts can conduct organization-wide risk assessment using StaffCop dedicated Risk dashboard. Risk can be profiled by users, departments, or by system objects, reports can be derived by severity of risks or by how many times security violations occurred, and Unique Risk Scores helps you identify high-risk users or policies so that plans can be created for treating the risks.


Compliance Management
Compliance is an increasingly challenging task: requiring organizations to manage multiple risk factors across an evolving technology landscape, while also ensuring appropriate user behavior to fulfil the stringent requirements of today’s widely-accepted regulatory standards, such as GDPR, HIPAA, PCI DSS, ISO 27001, NIST and others. Organizations that fail to remain compliant risk severe financial and reputational consequences. Regardless of the industry you are in, you need a solid compliance management solution that can help you attain compliance and then assists you in staying compliant with continuous oversight. Additionally, the solution should provide you with a burden of proof in case of an audit.
Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states..
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results.
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia




