- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
For Financial Sector
Unified User Activity Monitoring, Insider Threat Prevention, Cyber
Security and Compliance Management in a Single Solution
Request demoSecurity and Compliance Management in a Single Solution
StaffCop for Financial Services: Identify and Stop Insider Threats
Given that financial firms deal with money, intellectual property, trade secrets and personal information, they are prime targets for attacks from both internal and external actors.
While outside threats to the financial industry are significant, the biggest source of threat comes from the inside. Additionally, a majority of insider attacks are carried out by “inadvertent actors”, such as employees who succumb to phishing attacks. There are also threats which might appear external but are actually insider threats in disguise. For instance, a ’secure’ financial services company may expose itself to dangers when it grants access to its internal system to a fintech startup, who might have a weaker security system. Also, when banks outsource many operations to third-party vendors for efficiency and cost savings they open up a new avenue of threats for themselves and their customers.
To stay ahead of all these insider threats, financial services organizations need to widen their cybersecurity measures to include insider threat detection and data loss prevention solutions as part of their security toolbox. This will also enable them to comply with security and data privacy regulations.
StaffCop Combines Activity Monitoring, Threat Detection and Data Loss Prevention into a Single Integrated Solution
StaffCop is built to help the financial sector address data loss, cybersecurity and insider threats with its user activity monitoring, insider threat detection and data loss prevention solution. With StaffCop, financial services organizations can execute effective endpoint monitoring and ensure adherence to regulatory compliance when it comes to protecting sensitive financial and personal data. Here are a few ways StaffCop can assist financial services organization:
StaffCop allows organizations to automatically locate sensitive data and detect when it’s at risk.
It prevents data and IP theft, sabotage, fraud and other insider threats.
By identifying when a user saw privileged information, StaffCop detects insider threats.
Controls third-party access to confidential data.
StaffCop prevents document exfiltration over external drives, Cloud applications like Office 365, social media, email or file sharing sites like Dropbox, Google Drive.
It blocks the implementation of unauthorized applications to minimize scam, ransomware, and malware or virus infection.
Ensures organizations conform to regulatory compliance.
1
Real-Time User Activity Monitoring for Early Warning
The real-time monitoring system allows organizations to monitor all user activity covering 22+ system objects like: web pages, apps, email, file transfers, instant messaging, social media and more.
2
Productivity Analysis
Once you've set the applications and websites you consider productive, StaffCop will provide you with in-depth reports on how your employees and departments spend their time. Thus, allowing us to identify high performing employees and those who need improvement.
3
Detect Insider Threats with Intelligent Behavior Analysis
With StaffCop’s intelligent behavior analysis you can detect malicious activity and anomalies that indicate deviation from normal behavior.
4
Investigate Data Leak Incidents with Digital Forensics and Audit
Session recording, alert reports and immutable logs provide a vast collection of forensic data to locate the source and target with pinpoint accuracy when an incident occurs. Recordings can be used as evidence for further investigation or legal purposes.
5
Preventive Defense with Powerful Policy and Rules Engine
StaffCop allows you to create your own rules with an intuitive, visual Policy & Rules editor. Discover and group classified and sensitive data to apply exfiltration prevention rules. And leverage identity-based authentication, privileged user monitoring and the principle of least privilege (POLP) to prevent unauthorized access or tampering.
6
Protect Your Firm from 3rd-Party Threats:
Prevent sabotage and data theft by monitoring external and privileged users like third party vendors, remote users and IT admins who have access to your critical systems.
Financial Services is one of the Most Vulnerable Industries to Internal and External Threats:
Financial Services has the Highest Cost of Cyber Crime
According to Accenture, in 2017 cybercrimes in the financial sector had the highest annualized cost. Source: Accenture
$28M+ Average Annualized Cost of Cyber Crime
A huge number of Cyber Attacks are Financially Motivated
Findings from a 2018 Breach Investigation Report showed that 76 percent of cyber-attacks are motivated by money. Source: Verizon.
76%
of Cyber Attacks are Financially Motivated
Financial Services Firms are Attacked 300X More
Based on a Forbes' report a typical U.S. business is attacked 4 million times per year, whereas a U.S. financial services firm is attacked 1 billion times per year. Source: Forbes.
1B/Yr is How Often a Typical U.S. FS Firm is Attacked
15% Malicious Insider
Inadvertent Users are One of the Main Reasons of Threats
According to IBM 53% of insider attacks come from inadvertent actors and financial service firms experience the highest level of threat from these actors. Source: IBM.
53% Insider Attacks are carried out by Inadvertent Users.
StaffCop Helps You Comply With SEC Cybersecurity Guidelines:
Data Inventory
– Detailed inventory of assets, information and users
With its monitoring agent, StaffCop allows you to keep track of all your employees, endpoint, and data repositories.
Cyber security
– Penetration testing
– Security monitoring and audit
– Access control
– Reporting
– Security monitoring and audit
– Access control
– Reporting
StaffCop’s Policy & Rules Editor lets you conduct mock tests and drills for insider threats and offers detailed alerts and reports for data leaks and breach incident investigation.
Maintenance
– Vulnerability scan
– Patch management
– Patch management
Identify high risk users, failing policies and applications before they can wreak havoc with StaffCop’s dynamic risk scoring and vulnerabilities scanning.
Establish & enforce controls
– Acceptable use policy
– Third-party vendor activity log
– Termination of access
– Third-party vendor activity log
– Termination of access
StaffCop lets you track and implement security rules for external and privileged users like third-party vendors, remote users and IT admins.
Mandatory training
– Employee education and training
You can train new employees using insights derived from various reports and etiquette rules.
Management
– Engagement of senior management
StaffCop’s Enterprise dashboard enables senior management and CSO to protect their organization’s security health with real-time threat reports, user activity KPIs and risk trends.
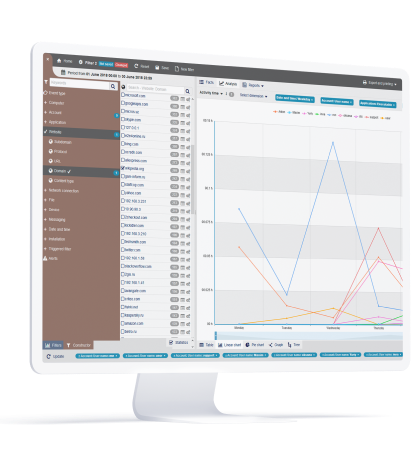
Establish Organization-
Wide Visibility and Control
Wide Visibility and Control
StaffCop has built-in features that allows it to visually record every action that a user makes for over 22 objects including screen, apps, websites, files, emails, etc. All objects can be adjusted to take into consideration what needs to be monitored and who has access to the monitored records. You can also control who you want to monitor, how much you want to monitor, when and for how long, thus you can have instant administrative oversight and still meet privacy requirements.
Data Loss Prevention & Egress Control
StaffCop’s exfiltration and egress controls allow you to monitor and prevent illicit sharing of information. For instance, File Transfer rules to prevent the use of removable media.
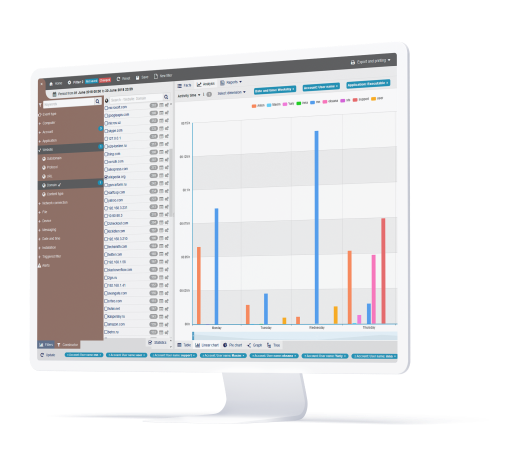
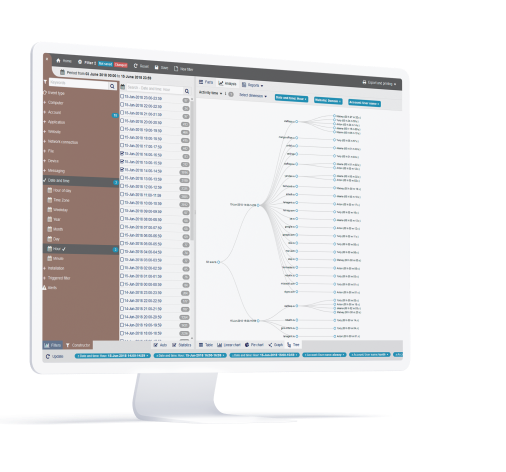
Behavioral Anomaly Detection
StaffCop allows you to define what constitutes dangerous user behavior, then uses its sophisticated anomaly engine to automatically detect when a user, department, or group deviates from their normal parameters or exceeds acceptable risk levels. Once a threat is detected, it notifies appropriate authorities, locks out the user or takes remote control of the compromised system.
Privileged User and Third-Party Monitoring
StaffCop allows organizations to create profiles for employees and third parties and define what information and system resources each profile can access. Further rules can be established by behavior policies so that access to sensitive information is segregated by the organization’s security policy, or on a need-to-know basis.
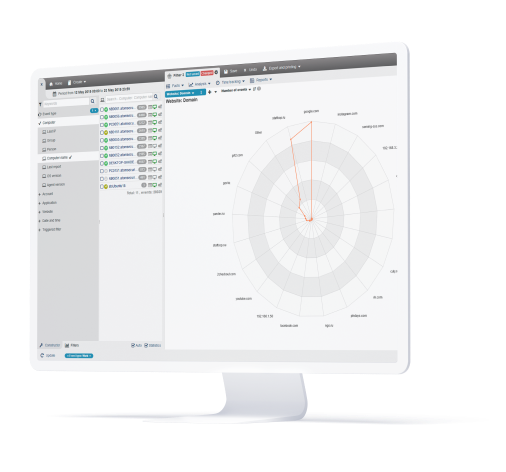

Digital Forensics and Auditing
Detailed alerts including any security incidents and what actions were taken can be viewed. Warning messages can be programmed to inform the users about nonconformity and influence corrective behavior. Session recordings and history playback can be leveraged to view user’s desktop for audit and evidence gathering purposes
Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states.
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results..
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more.
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



