- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
GDPR Compliance
Request demoGeneral Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) took effect in May 2018, requiring all organizations handling the personally identifiable information (PII) of European Union citizens to keep that data secure. Organizations who fail to comply are subject to substantial penalties.
GDPR requires organizations to implement policies and procedures with respect to collection, treatment and management of data, a plan to detect a data breach, regularly evaluate the effectiveness of security practices, and document evidence of compliance. With that, GDPR effectively mandates organizations to implement best practices for privacy and data security.
GDPR requires organizations to implement policies and procedures with respect to collection, treatment and management of data, a plan to detect a data breach, regularly evaluate the effectiveness of security practices, and document evidence of compliance. With that, GDPR effectively mandates organizations to implement best practices for privacy and data security.
StaffCop for GDPR helps organizations conform with ongoing compliance requirements with its extensive user activity monitoring, data exfiltration protection, audit, reporting and forensics capabilities.
1
Privacy-focused monitoring
Real-time monitoring protects sensitive data from insider threats while dynamic blackout and selective recording features ensure privacy for personal data.
2
Ongoing compliance enforcement
Behavior and activity monitoring platform continuously enforces policies and takes immediate action on detection of anomalies or rule violations..
3
Data discovery and classification
Find and categorize personally identifiable data to apply data privacy and data exfiltration rules.
4
Authentication and access control
Identity based authentication and segregated access control prevent unauthorized PII access or sharing.
5
Data risk mitigation
Identify high risk employees, policies and system components that may put your GDPR and other compliance initiatives at risk.
6
Collect evidence with conformance
Screen recording only during policy violation incidents allows for collection of forensic data, while conforming to the privacy and record keeping boundaries set by GDPR.
7
Audit ready
Session recording and immutable logs keep track of access, entitlement and rectification related information.
8
Reporting for the entire compliance team
Identify high risk employees, policies and system components that may put your GDPR and other compliance initiatives at risk.
Data breach is a costly challenge facing privacy
ONLY 35%
of organizations have a data breach reporting procedure that is aligned with GDPR requirements. Source: Deloitte.
$20M / 4%
of revenue is the maximum penalty for organizations who fail to comply with GDPR. Risk of litigation, loss of brand reputation and customer loyalty are also likely outcomes..
$350M
damages is associated with a large data breach. For smaller breaches, the average is about $$3.86 Million. Source: IBM and the Ponemon Institute.
~$13.4B
data records got lost or stolen since 2013. Everyday, approximately 6.1 Million records are lost or stolen. Source: Gemalto..
Data breach is a costly challenge facing privacy
StaffCop for GDPR provides user activity and data exfiltration monitoring capabilities to help organizations detect, investigate, and report on data breaches.

Identify
Leveraging advanced fingerprinting, OCR and tagging technology, StaffCop identifies personal and sensitive data in structured and unstructured information across organization data stores.

Protect
StaffCop leverages its activity monitoring and data loss prevention capabilities to defend confidential and private information from unauthorized access, sharing, attack and misuse.

Detect
StaffCop’s powerful behavior-based policy and rules engine casts a strong detection net over the entire organization, allowing for quick detection of insider threats and data breach incidents before it happens.

Responde
Real-time notification and immediate actions proactively defend against data exfiltration, malicious or accidental insider threats and data breaches. In case of an incident, pinpoint the exact cause and source of the incident with readily available audit and forensic data.
.svg?v=2020-10-30T02:15:40.681Z)
Report
Meet GDPR record keeping requirements with detailed incident reports, alerts and session recordings. Exportable reports can be shared with the Controller, DPO, auditors and other members of the compliance team.
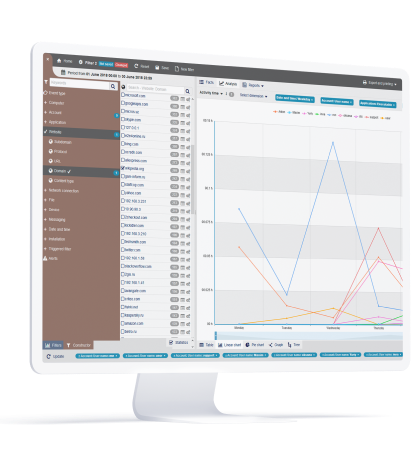
Principles relating to processing of personal data (GDPR Article 5)
Teramind for GDPR can ensure data is processed lawfully and not exfiltrated to unauthorized systems and mediums. Data classification can be set to identify personal data and then policies and rules can be created using advanced OCR and fingerprinting features to detect and restrict access to such data automatically.
Processing of special categories of personal data (GDPR Article 9)
Article 9 lays out further requirements for special categories of personal data. For example, Member States may maintain or introduce further conditions, including limitations, with regard to the processing of genetic data, biometric data or data concerning health.
Teramind for GDPR features built-in classifications for health-related data such as DNA profiles, National Health Services numbers, disease and drug names, and more. Custom data types can be created for your unique needs.
Teramind for GDPR features built-in classifications for health-related data such as DNA profiles, National Health Services numbers, disease and drug names, and more. Custom data types can be created for your unique needs.

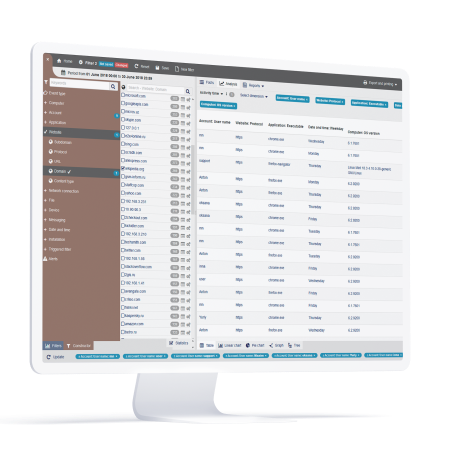
Data protection and design by default (GDPR Article 25)
eramind for GDPR can ensure data is processed only in the context it is required to be processed. Monitoring settings can be configured to only record the necessary information. For example, keystrokes or screen capture can be disabled when a user enters their personal banking site or personal emails.
Organizations can implement Teramind for GDPR with specific monitoring features and recording of events only at policy violations, narrowing the scope of user activity recording and ensuring a privacy-friendly implementation. Administrators' privileges can be limited with tiered access to only view specific sets of data. Custom alerts and prompts can be set up to inform users what data is collected and allow them to acknowledge any action being taken.
Organizations can implement Teramind for GDPR with specific monitoring features and recording of events only at policy violations, narrowing the scope of user activity recording and ensuring a privacy-friendly implementation. Administrators' privileges can be limited with tiered access to only view specific sets of data. Custom alerts and prompts can be set up to inform users what data is collected and allow them to acknowledge any action being taken.
Record of processing activities (GDPR Article 30)
GDPR requires organizations to maintain an up-to-date record of the locations and usage of personal information and product/demonstrate safeguards used to protect the data. This could be information in files, databases, email, unstructured data, backups, DMS, knowledge bases, or anything else that houses data.
Teramind for GDPR can help the Controller and the CDO identify this information and record who’s accessing what data, how the data is flowing through the organization and then create perimeter rules to safeguard their access or usage
Teramind for GDPR can help the Controller and the CDO identify this information and record who’s accessing what data, how the data is flowing through the organization and then create perimeter rules to safeguard their access or usage
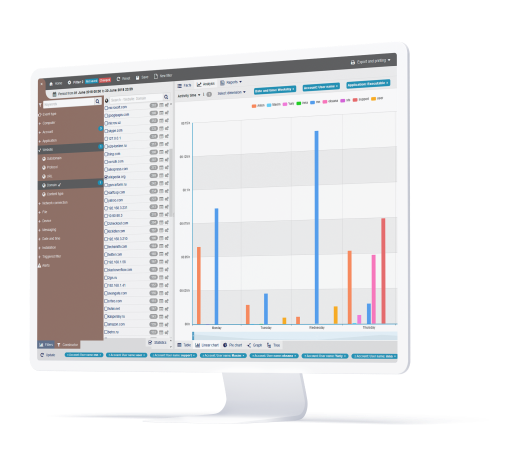
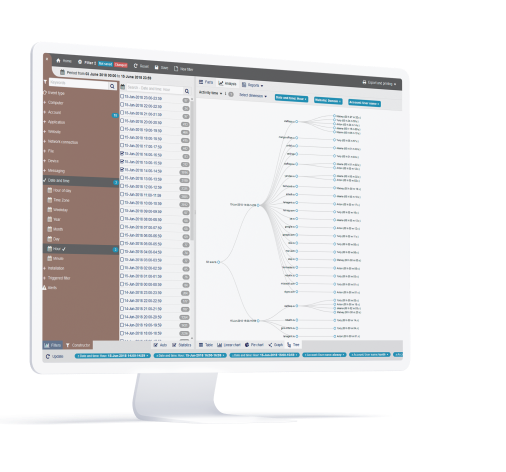
Security of processing (GDPR Article 32)
Part of Article 32 states that the Controller and the Processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk.
Teramind for GDPR is well suited to help implement many of these security requirements. For example: implement access profiles for each staff, restrict or block sharing of encrypted content, limit use of FTP/Cloud sharing sites, prevent the viewing of sensitive data by employees, prevent unauthorized decryption operations on files and more.
Teramind for GDPR is well suited to help implement many of these security requirements. For example: implement access profiles for each staff, restrict or block sharing of encrypted content, limit use of FTP/Cloud sharing sites, prevent the viewing of sensitive data by employees, prevent unauthorized decryption operations on files and more.
Notification of a data breach (GDPR Article 33)
Teramind for GDPR can provide full forensics with respect to a data incident, and a video recording of the event. Detailed alert reports can be exported including any security incidents and what actions were taken in minutes superseding the 72 hour limit set by GDPR. Session recordings and history playback can be used to provide proof for further forensic investigation.

Supporting the data protection officer (GDPR Article 38)
Some key responsibilities of the DPO is advising the Controller on various GDPR initiatives and monitor the effectiveness of the compliance measures and identify any risk associated with data processing operations.
To help the DPO with their role, Teramind for GDPR has a role-based access management system ensuring that both internal and external users are monitored and audited properly. Additionally, there’s a Risk dashboard that identifies policies, rules, personnel and system objects that are at risk.
To help the DPO with their role, Teramind for GDPR has a role-based access management system ensuring that both internal and external users are monitored and audited properly. Additionally, there’s a Risk dashboard that identifies policies, rules, personnel and system objects that are at risk.
Monitoring of approved codes of conduct (GDPR Article 41)
Teramind for GDPR monitors all employee, contractor and third-party vendor activity including file access, apps and website usage and all other interactions within the local, network or Cloud environments. Business etiquette rules can be created to train the users about nonconformity and influence corrective behavior..

Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest..
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states..
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results..
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



