- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
For Legal
Request demoLaw firm insider threat management
In today’s highly regulated business landscape, law firms are faced with the ever-evolving challenge of tackling their insider risk problems as it relates to protecting attorney-client privileged information and client/matter data, ensuring the security of the work product offshored, and securing access to critical systems by privileged users and third-party vendors/contractors.
StaffCop for Legal is designed to assist law firms to address these challenges and demonstrate effective oversight to compliance initiatives to clients.
StaffCop for Legal is designed to assist law firms to address these challenges and demonstrate effective oversight to compliance initiatives to clients.
Complience management
Since clients now require law firms to adhere to regulatory standards such as AML/KYC, HIPAA, ISO27001/27002, GDPR that secure their sensitive data, it is crucial for legal organizations to adopt solutions that ensure compliance.
1
Controls to enforce safety of client/matter data and work-product stored in firm systems and repositories
2
Oversight, audit and logs of all actions for all employees at the firm
3
Privileged user monitoring, session recording, with videos, searchable logs, and audit trail for forensics
4
User behavior analytics to eliminate false positives, and identify anomalous behavior
5
An immutable log of actions that vividly product/demonstrate all activity as it relates to firm desktops, laptops and content
6
Ability to set up real-time alerts to track suspect activities
Data breach is a costly challenge confronting privacy
53 %
of all attacks resulted in a financial loss of more than US $500,000, including, but not limited to, lost revenue, customers, opportunities, and out-of-pocket costs.
$209M
The FBI reported that $209M was paid in ransom in the first quarter of 2016, while just $24 million in ransom payments was made in all of 2015.
67%
of businesses identified privileged users as a top cloud security concern.
~$12B
estimated annual losses for the US from cybercrime targeting IP and roughly $50 billion to $60 billion globally
StaffCop helps to comply with
ISO 27001
ISO 27001
StaffCop Enterprise can significantly help you meet ISO 27001 demands. The flexibility of settings makes it perfect to fit any Information Security Management System (ISMS). PDCA (Plan-Do-Check-Act) cycle lies in the core of the standard, so let’s take it with StaffCop step-by-step.

Plan
At this stage you should establish the internal policy of the company regulating creation and distribution of information (ISMS) within and beyond the company. The corporate information and access to it should be classified and divided with different access rights for different groups of employees. For example, your employees should work only with a limited number of web-sites and applications, the PC of the secretary is the only one which can print documents and the sales department is the only department with access to the customers’ database.

Do
The implementation is done through creating a number of fully customized filters and policies. It’s all carried out in the administrative interface of StaffCop to be applied on the workstations. The policies and filters can be easily modified at any moment. StaffCop is deployed in your corporate network and it doesn’t send any data outside providing high level of information security. It can work in closed networks, the ones that don’t have internet connection.

Check
The monitoring is carried out in the same administrative interface. A number of administrators can be assigned access right corresponding to the level of the responsibility they carry. For example, each head of a department can monitor information on PCs belonging to his or her department. The alerts on violations of ISMS will be sent to the specified e-mail addresses, be it a security officer or the company owner. Documents can be easily searched for classified information, and if it’s contained in images or PDF, the text will be recognized.

Act
StaffCop Enterprise can track huge amount of information that can be used to analyze user behavior and estimate. Use pre-set and customized reports to analyze data and visualize the resulting output. There are quite handy embedded tools, such as heat map and anomalies detector that could help you track behavior trends and deviations. With experience gained and data collected the ISMS should be corrected in a corresponding way, which means both organizational means and configuring of StaffCop polices.
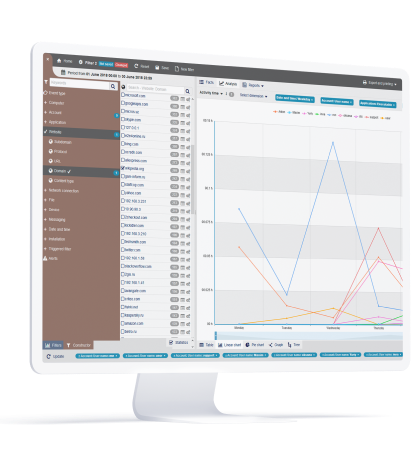
User session recording, live view and playback
StaffCop’s Session Recording feature captures all user activity and screen content. With this function, you can:
Know and have forensic evidence, if your users are engaged in unproductive or harmful activities while at work.
Take control of a user's desktop in a potential breach event.
With the components such as immutable logs, alert reports and audit trails, the recording can serve as forensic evidence for investigation.
The insight derived from the reports and recordings can be leveraged to train employees about security best practices.
Privileged user monitoring
Because of their access to critical information systems containing client/matter data, privileged users can cause severe damage to a law firm, if they have malicious intent. They can leak, steal or potentially destroying client/matter data and work product. To prevent these insider threats, StaffCop offers:
Power-user rules to check for backdoor account creation, attempt to gain additional system privileges etc.
Real-time alerts when a privileged user tries to tamper with sensitive systems, databases or content.
Immutable session log that keep a permanent record of all privileged user actions.

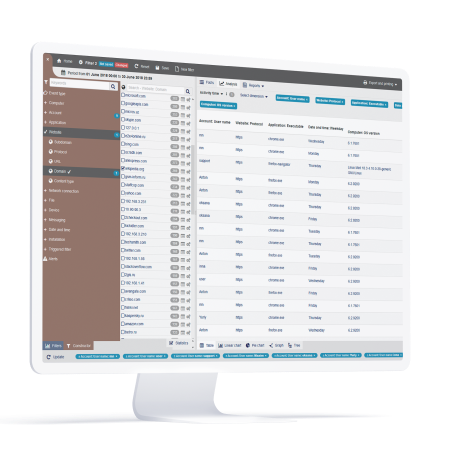
Intelligent session mining with OCR
StaffCop can collects all data on a computer screen, including text in images and apply OCR technology to provide the firm with the ability to:
Search for certain keywords and find any relevant content that was visible to the user, using regular expressions or natural language.
Find out which users have seen relevant information to ensure ethical walls remain in place and report any violations.
Develop rules that send an alert when certain text appears on screen.
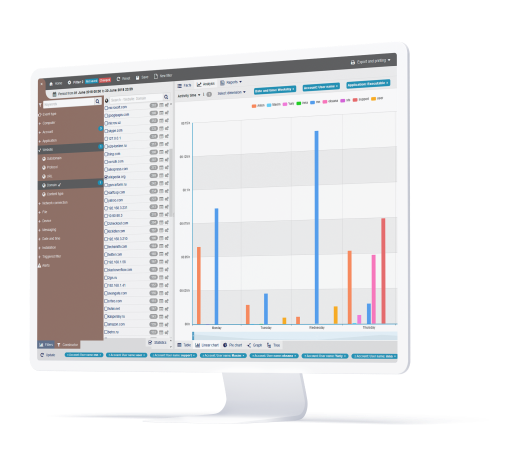
Process and productivity optimization
With work product offshored and contracted out on a regular basis, it’s essential to be able to monitor and improve the process and productivity of the extended legal workforce. StaffCop can assist by offering a framework within which your law firm can:
Classify apps and websites you consider productive and provide in-depth reports on their usage.
Detailed reports for productivity KPIs like session, active, productive, unproductive and idle time.
Sends automated alerts to discourage excessive idling.
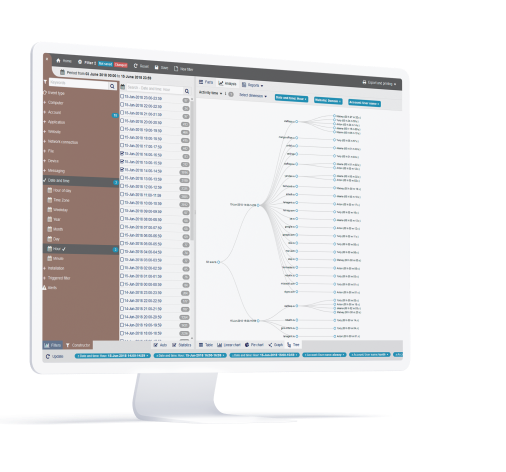
Policy and rules engine
With StaffCop’s visual Policy and Rules creation engine, law firms can establish:
Rules and policies to monitor and secure client/matter and other sensitive data from insider threats and breaches.
The visual Policy and Rules Editor allows administrators to define highly complex rules for very specific use cases with oversight on all internal and external disk activity, keystrokes, application usage, and much more.
Utilize black/whitelisting, define safe or restricted apps and websites, and do much more.
Privacy-aware recording and monitoring
StaffCop allows firms to have complete control over when, who and how much to monitor, when to record and when not to. StaffCop is flexible to accommodate all use cases:
Track activity and alert only, with no user-session recording
Specified working hours monitoring
Define which types of data are monitored for specific users or departments. E.g, monitor only printing documents for the accountant, only email and messengers for the sales department, and so on.

Revealed or stealth desktop agent
You can either deploy StaffCop with a revealed desktop agent, whereby users are aware of the StaffCop system and its monitoring functions. Or, launch the desktop agent in stealth mode with no visible controls to the end-users being monitored.
With the revealed agent you can:
Users can see the StaffCop icon in the taskbar with the address of the StaffCop Server aggregating the data from this agent.
Users will be required to provide reasons for absence, if there is no activity registered for a specified period of time.
Allows you to control mouse and keyboard of a remote desktop in real-time
Data loss prevention
Compliance, competition and customer trust means law firms have to safeguard client/matter information and work product. To ensure data safety and integrity, StaffCop provides a robust, four-step data loss prevention process:
First, it allows you to define what constitutes sensitive or classified data.
Creates a security perimeter by setting rules for how the data should be handled.
Automatically thwart any rule violation incident with actions that block, notify, or warn.
In case of a data breach, pinpoint the exact cause and source of the incident with audit and forensic data available in the StaffCop system.

Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states.
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results. .
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



