- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
Retail & Ecommerce
Cyber Security
Cyber Security
Unified User Activity Monitoring, Insider Threat Prevention, Cyber
Security and Compliance Management in a Single Solution
Request demoSecurity and Compliance Management in a Single Solution
StaffCop for Financial Services: Identify and Stop Insider Threats
The retail and e-commerce industry faces a growing threat of cybersecurity breaches and stolen information. Data breaches do not only cost retailers millions of dollars, they also negatively impact their brand reputation.
Compounding the issue is the fact that online retailers and e-commerce sites are more susceptible to cyber-attacks due to their exposure on the public internet and the Cloud. They are also increasingly capturing a large amount of personal information and behavioral data to enable personalized experience to their customers. This means, they now have to safeguard volumes of different data types, and when a breach occurs, they are held liable.
All these factors make it imperative for retailers to implement strict restrictions on data access, monitor employees who work with sensitive information, and have the capability to identify insiders, often the main cause of cybersecurity breaches, whether intentionally or inadvertently.
StaffCop Addresses Activity Monitoring, Threat Detection, Data Loss Prevention Needs with a Single Unified Solution
StaffCop’s user activity monitoring, insider threat detection, and data loss prevention solution can assist the retail sector address data loss, cybersecurity and insider threats With StaffCop, retail companies can implement effective endpoint monitoring to ensure adherence to regulatory compliance when it comes to protecting sensitive financial and personal data. Here are a few examples of what retailers can achieve with StaffCop:
Real-Time User Activity Monitoring: provides 24/7 visibility across your departments and vendors.
Endpoint Data Loss Prevention: protects sensitive data in residing in Point-of-sale (POS) systems, back-office workstations, shared over the network or on the Cloud.
Risk-Based Insider Threat Prevention: Prevents any sabotage, collusion or other malicious intent by employees and privileged users.
1
Auto discovery of card number data
StaffCop’s built-in templates can be used to develop card numbers with the implementation of the Luhn algorithm. And its advanced OCR and digital fingerprinting is effective in content discovery.
2
Protect Your Business from Data Breaches
Real-time user activity monitoring enforces classified financial data rules for websites, apps, emails, social media and automatically warn if unauthorized access is detected.
3
Implement Solid Access control
StaffCop offers identity authentication and segregated access levels to minimize data compromises. It can also be leveraged to limit transfers of cardholder data on local, network, Cloud and external storage.
4
Protect Your Retail Operations from Insider and 3rd-Party Threats
Restrict privileged user’s access to cardholder/transaction servers and databases and monitor third parties who have access to your critical systems with StaffCop.
5
Comply with PCI DSS, GLBA, SOX, GDPR and Others
The solution also offers reports on Compliance (ROC) with Digital Forensics and Audit. Its session recording and immutable log monitor all user activity related to cardholder data while flexible Policy & Rules Editor allows for creation of new rules for the evolving compliance landscape.
Financial Services is one of the Most Vulnerable Industries from Both Internal and External Threats
Retail is a prime cybercrime target, particularly in the u.s.
A 2018 Thales study found, three quarters (75%) of U.S. retail have been breached at least once in the past, ahead of 60% for Global retail.
75% of U.S. Retail was breached at Least Once in the Past
Data breaches have a huge impact on customer loyalty
According to a report by Gemalto, if a company suffered a data breach, 70% of consumers would stop doing business with it.
70% of Consumers Would Abandon a Breached Company
E-commerce websites are used by hackers using stolen data
Based on a report by Business Insider, 80-90% of the people who log in to a retailer's e-commerce site are hackers using stolen data.
80%+ of E-commerce Website Users are Hackers in Disguise
Card fraud losses will impact banks and merchants
According to a report by Nilson, card fraud losses by banks and merchants worldwide are expected to rise to $32.82 billion by the end of 2019.
$32B+ Estimated Worldwide Card Fraud Losses by 2019
StaffCop Helps Energy & Utilities Companies Protect Sensitive Data
Brick and mortar stores
– Personally Identifiable Information (PII): name, address, date of birth, social security number, driver's license etc.
– Payment Card Industry Data Security Standard (PCI DSS) i.e. cardholder data, debit card no.
– Supplier/vendor contracts.
– Payment Card Industry Data Security Standard (PCI DSS) i.e. cardholder data, debit card no.
– Supplier/vendor contracts.
Online retailers / ecommerce
– Customer data – PII + PCI.
– User preferences and buying patterns.
– Business processes.
– Session logs, site cookies, customer credentials, support pin, black/white listed IPs, public keys etc.
– User preferences and buying patterns.
– Business processes.
– Session logs, site cookies, customer credentials, support pin, black/white listed IPs, public keys etc.
Сorporate data
– Business processes and strategic plans.
– Price/cost/supplier/customer lists.
– Source code, formulas, patents and other type of IPs.
– Acquisition plans, M&A announcements, legal documents and other confidential matters.
– Payroll, accounting and financial data.
– Price/cost/supplier/customer lists.
– Source code, formulas, patents and other type of IPs.
– Acquisition plans, M&A announcements, legal documents and other confidential matters.
– Payroll, accounting and financial data.
And more...
– Billing/invoice, tax/VAT, GST/HST, enrollment and payment related data.
– GDPR special data categories (trade union data, biometric, geo location).
– For Official Use Only (FOUO), Confidential and Protected file tags.Federal
– Tax Information (FTI), Covered Financial Information (GLBA) etc.
– GDPR special data categories (trade union data, biometric, geo location).
– For Official Use Only (FOUO), Confidential and Protected file tags.Federal
– Tax Information (FTI), Covered Financial Information (GLBA) etc.
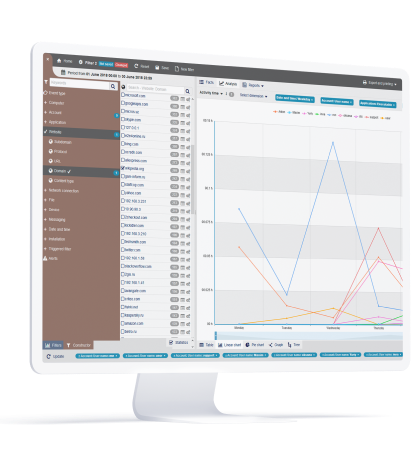
Real-Time Visibility and Control
StaffCop visually records every action that a user makes on your OT and IT systems and cloud, DMZ for 22+ system objects. Each object can be programmed to take into consideration what needs to be monitored and who has access to the monitored records. You can specify who you want to monitor, how much you want to monitor, when and for how long.
Automated Data Discovery and Classification
StaffCop has built-in templates for many classified and unclassified data types to protect your customer data, IP and other sensitive information.

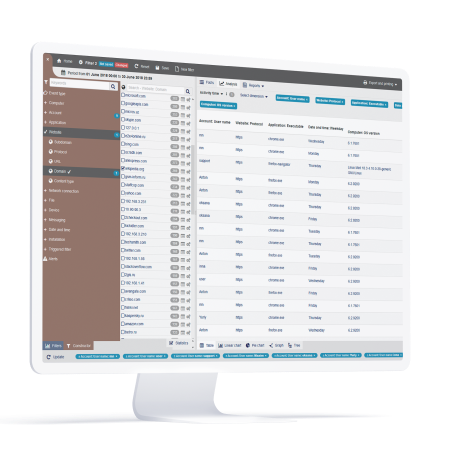
Powerful Policies and Rules Engine
StaffCop allows you to create your own rules with an intuitive, visual Policy & Rules editor. Discover and group classified and sensitive data to apply exfiltration prevention rules. And leverage identity-based authentication, privileged user monitoring and the principle of least privilege (POLP) to prevent unauthorized access or tampering.
Endpoint Data Loss Prevention & Egress Control
StaffCop’s exfiltration and egress controls allow you to monitor and prevent illicit sharing of information. For instance, File Transfer rules to prevent the use of removable media. Clipboard rules stop the sharing of confidential information like customer data outside the CRM.
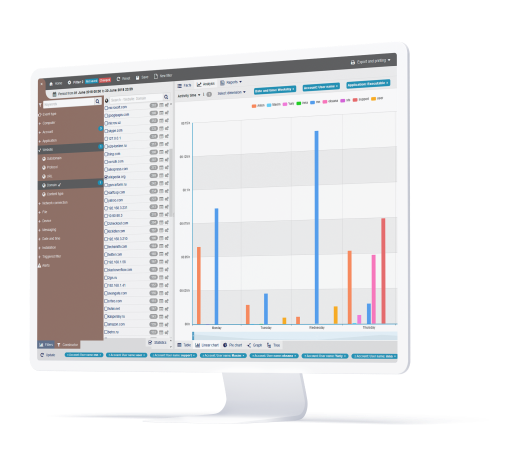
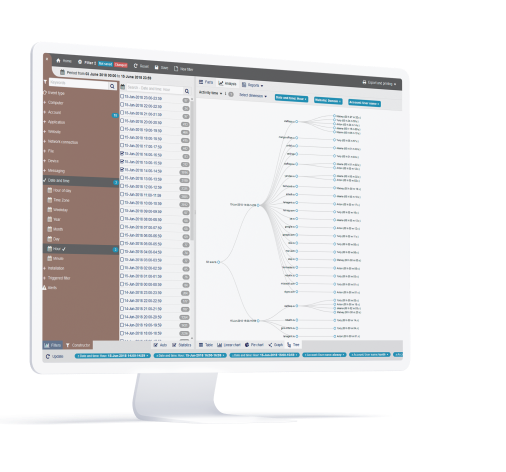
Behavioral Anomaly Detection
StaffCop allows you to define what constitutes dangerous user behavior, then uses its sophisticated anomaly engine to automatically detect when a user, department, or group deviates from their normal parameters or exceeds acceptable risk levels. Once a threat is detected, it notifies appropriate authorities, locks out the user or takes remote control of the compromised system.
Privileged User and Third-Party Monitoring
StaffCop allows organizations to create profiles for employees and third parties and define what information and system resources each profile can access. Further rules can be established by behavior policies so that access to sensitive information is segregated by the organization’s security policy, or on a need-to-know basis.
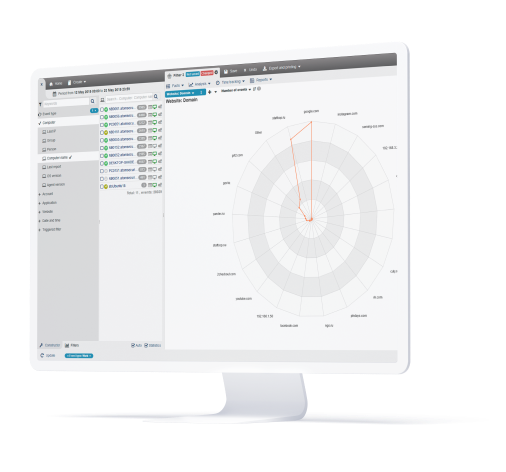

Digital Forensics and Auditing
Detailed alerts including any security incidents and what actions were taken can be viewed. Warning messages can be programmed to inform the users about nonconformity and influence corrective behavior. Session recordings and history playback can be leveraged to view user’s desktop for audit and evidence gathering purposes
Compliance Management
Compliance is an increasingly challenging task: requiring organizations to manage multiple risk factors across an evolving technology landscape, while also ensuring appropriate user behavior to fulfil the stringent requirements of today’s widely-accepted regulatory standards, such as GDPR, HIPAA, PCI DSS, ISO 27001, NIST and others. Organizations that fail to remain compliant risk severe financial and reputational consequences. Regardless of the industry you are in, you need a solid compliance management solution that can help you attain compliance and then assists you in staying compliant with continuous oversight. Additionally, the solution should provide you with a burden of proof in case of an audit.

Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states.
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results. ..
.
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



