- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
PCI DSS Compliance
& Certification
Request demo& Certification
PCI DSS - Payment Card Industry Data Security Standards
Payment Card Industry Data Security Standard (PCI DSS) regulates any business that collects or processes cardholder data. The overall objective of PCI compliance is to propagate data protection techniques and mitigate the risk of credit and debit card fraud, and to ensure the security and privacy of financial and personal information.
Failure to meet PCI DSS requirements may lead to substantial penalties and fines, suspension of credit card acceptance by a merchant’s credit card account provider, possible civil litigation from breached customers and other opportunity costs due to brand/reputation damage.
PCI has set six goals with twelve steps in Data Security Standard for its Merchants & Processors category. Further more, it has strict compliance validation and reporting requirements that involves verification and confirmation that the recommended security controls and procedures are in place and properly followed.
Failure to meet PCI DSS requirements may lead to substantial penalties and fines, suspension of credit card acceptance by a merchant’s credit card account provider, possible civil litigation from breached customers and other opportunity costs due to brand/reputation damage.
PCI has set six goals with twelve steps in Data Security Standard for its Merchants & Processors category. Further more, it has strict compliance validation and reporting requirements that involves verification and confirmation that the recommended security controls and procedures are in place and properly followed.
StaffCop is designed to assist the public sector address data loss, cybersecurity and insider threats with its insider threat detection and data loss prevention solutions. With StaffCop, government entities can implement effective endpoint monitoring to ensure adherence to regulatory compliance and standards including NIST, FAR/DFARS, FDCC, FedRamp, FISMA, Insider Threat Executive Order and more.
1
Auto discovery of card number data
Built-in templates for card numbers developed with the implementation of Luhn algorithm. ‘On the fly’ content discovery with advanced OCR and digital fingerprinting.
2
Protection from data breaches
Real-time user activity monitoring prevents accidental or malicious insider threats and data breaches. Enforce classified financial data rules for websites, apps, emails, social media etc. Automatically warn if unauthorized access is detected.
3
Implement solid access control
Apply Identity authentication and segregated access levels to minimize data compromises. Restrict transfers of cardholder data on local, network, Cloud and external storage. Monitor privileged users access to cardholder servers and databases..
4
Vulnerability and risk management
Identify vulnerable employees, policies and system components. Develop contingency plans with risk assessment and analytics.
5
Report on compliance (ROC)
Session recording and immutable log keep track of all user activity related to cardholder data. Detailed reports of all data breach incidents, rule violations and what actions were taken.
Cyber threats and data breaches are at an all time high
$150M+
estimated average cost of a data breach by 2020 as more business infrastructure gets connected. Source: Cybiant.
$500,000
is the maximum penalty per incident for security breaches when merchants are not PCI DSS compliant.
14.2M
credit card numbers were exposed in 2017, an 8X increase over 2016. Source: Experian.
$9.1B
is the value of payment card fraud losses in the USA in 2018. Source: Statista
Effectively Detect, Investigate, and Report on Data Breaches
StaffCop provides essential security monitoring capabilities to help you detect, investigate, and report on data breaches within retail/e-commerce or other card processing environments.

“Restricting access to cardholder data to only authorized personnel. Systems and processes must be used to restrict access to cardholder data on a “need to know” basis.”
StaffCop can be used for diversifying access to the cardholders’ data, which means that only authorized users will be able to work with files containing this kind of information.

“Identifying and authenticating access to system components. Each person with access to system components should be assigned a unique identification (ID) that allows accountability of access to critical data systems.”
Each user with authorized access to cardholders’ data will have a unique identification represented by its name. This is also true for the users of StaffCop – they can be assigned unique IDs and unique range of permissions.

“Restricting physical access to cardholder data. Physical access to cardholder data or systems that hold this data must be secure to prevent the unauthorized access or removal of data. Prevention by blocking channels.”
StaffCop can protect cardholder data against leakage by blocking information channels through which it may leak. For example, the PC containing this type of information can have USB and CD drives or e-mail applications blocked.

“Tracking and monitoring all access to cardholder data and network resources. Logging mechanisms should be in place to track user activities that are critical to prevent, detect or minimize impact of data compromises.”
StaffCop keeps track of all information associated with cardholder data and network resources and possesses all the instruments which may be used to prevent this data leakage, including the ability to instantly block the targeted PC. The card numbers are identified with the implementation of Luhn algorithm, so the administrator of the system will be timely notified about the actions with this data which gives him time to take preventive measures.
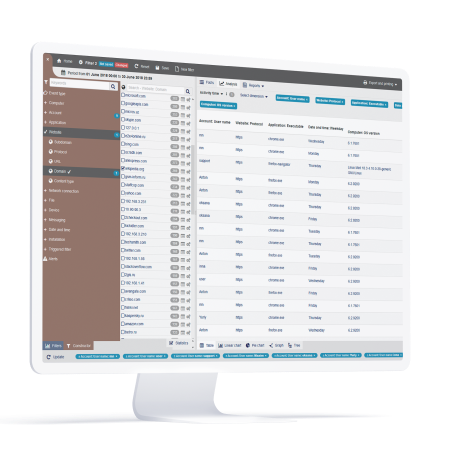
Access control and monitoring
Granular user activity monitoring, file tagging DLP module, layered access control for local, network and Cloud resources are just a few examples how StaffCop gives you full visibility and control over sensitive data.
Automated vulnerability management
Advanced behavior-based rule engine automatically prevents data loss and exfiltration events. Immediately get notified about harmful user activity or lock out user before any malicious or fraudulent attempt.
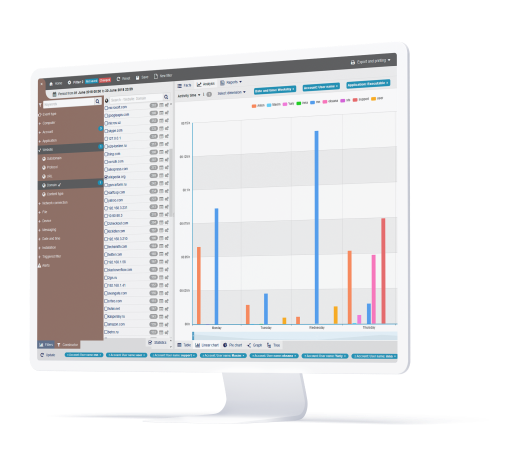
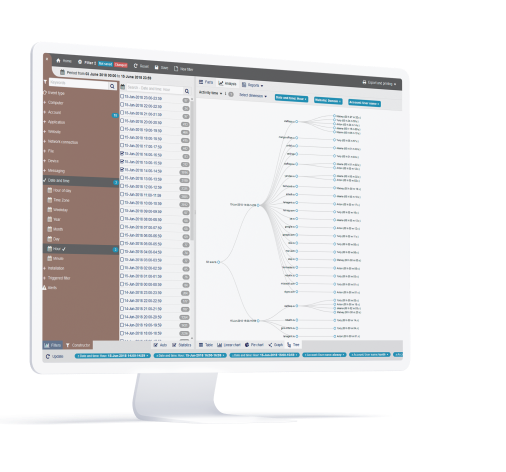
Reporting and audit
Detailed rule violation alerts, risk analysis reports, immutable logs and audit trails can serve as valuable sources for compliance reporting. Teramind makes your finding and observation tasks easier by identifying where card data is stores, how it’s accessed and finally prove that you have a system in place to enforce PCI data protection rules.
Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states.
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results.
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



