- 404
- Home
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
- 404
- index
- Remote Administration
- Employee Monitoring
- Insider Risk Management
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Purchase
- Request demo
- Solutions
- Demo request
- For Banks
Government & Public
Sector Cyber Security
Request demoSector Cyber Security
StaffCop for Government & Public Sectors
Some of the most coveted high value targets include federal departments and agencies such as defense, infrastructure, transportation, utility and intelligence. State & local government (SLG) agencies, particularly their e-government (E-GOV) arm regularly process citizens’ personal information that could be used by malicious actors for identity theft, impersonation, fraud and other crimes. The risk of data theft, exfiltration and similar crimes are compounded by the fact that government data is accessible by a large audience, including government employees, third-party contractors and vendors over multiple channels.
With StaffCop insider threat detection and data loss prevention solutions, data loss, cybersecurity and insider threats in the public sector can be significantly reduced. Thanks to StaffCop, government entities can implement effective endpoint monitoring to ensure adherence to regulatory compliance and standards including NIST, FAR/DFARS, FDCC, FedRamp, FISMA, Insider Threat Executive Order and more.
1
Real-time endpoint monitoring
StaffCop not only monitors all user activity over endpoints, network, servers but also the Cloud covering of over 22 system objects, including web, apps, email, files etc., and on-screen content in real-time.
2
Insider threat detection
StaffCop’s insider threat detection strategy includes creating policies and anomaly rules to catch suspicious, accidental or malicious threats. And using sophisticated risk algorithms to identify high risk users, vulnerable policies and system components.
3
Data security and integrity
To ensure data security, StaffCop identifies and categorizes classified and sensitive data, then applies exfiltration prevention rules.
4
Compliance support
Companies can also leverage StaffCop to develop activity and schedule-based rules to support several common compliance requirements like implementing audit trails (GDPR), limiting unauthorized login (ISO 27001), prevent unencrypted file transfers (PCI DSS), reporting, etc.
5
Digital forensics and incident response
Session recording, alert reports and immutable logs provide a wide array of forensic data to locate the source and threat vectors with pinpoint accuracy.
6
Instant reports
User activity, incident and risk reports, alert and session logs are provided for viewing and exporting from the dashboard.
Data breach is a costly challenge facing privacy
NO. 1
In 2017, government agencies were the number one target in terms of the number of records lost, stolen or compromised in 2017. Source: Gemalto.
$1.7M
$1.7M records were stolen by Edward Snowden, a contract systems administrator assigned to the NSA according to a report on Data Breach Today.
14M
Based on a report published on SC Media, 14M customer records were exposed in 2018 from GovPayNow, a payment gateway used by many government agencies.
48%
ICMA reveals that there is a 48% greater propensity for the government sector to suffer from malicious insider breaches than other sectors.
StaffCop helps to comply with
ISO 27001
ISO 27001
StaffCop Enterprise can significantly help you meet ISO 27001 demands. The flexibility of settings makes it perfect to fit any Information Security Management System (ISMS). PDCA (Plan-Do-Check-Act) cycle lies in the core of the standard, so let’s take it with StaffCop step-by-step.

Plan
At this stage you should establish the internal policy of the company regulating creation and distribution of information (ISMS) within and beyond the company. The corporate information and access to it should be classified and divided with different access rights for different groups of employees. For example, your employees should work only with a limited number of web-sites and applications, the PC of the secretary is the only one which can print documents and the sales department is the only department with access to the customers’ database.

Do
The implementation is done through creating a number of fully customized filters and policies. It’s all carried out in the administrative interface of StaffCop to be applied on the workstations. The policies and filters can be easily modified at any moment. StaffCop is deployed in your corporate network and it doesn’t send any data outside providing high level of information security. It can work in closed networks, the ones that don’t have internet connection.

Check
The monitoring is carried out in the same administrative interface. A number of administrators can be assigned access right corresponding to the level of the responsibility they carry. For example, each head of a department can monitor information on PCs belonging to his or her department. The alerts on violations of ISMS will be sent to the specified e-mail addresses, be it a security officer or the company owner. Documents can be easily searched for classified information, and if it’s contained in images or PDF, the text will be recognized.

Act
StaffCop Enterprise can track huge amount of information that can be used to analyze user behavior and estimate. Use pre-set and customized reports to analyze data and visualize the resulting output. There are quite handy embedded tools, such as heat map and anomalies detector that could help you track behavior trends and deviations. With experience gained and data collected the ISMS should be corrected in a corresponding way, which means both organizational means and configuring of StaffCop polices.
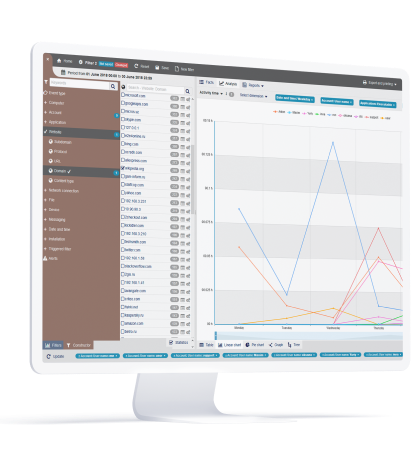
Establish Organization-Wide Visibility and Control
StaffCop visually records every action taken by an employee over 22 system objects including screen, apps, websites, files, emails, etc. Each object can be configured to take into account what needs to be tracked and measured and who has access to the monitored records. With StaffCop, you can determine which employees or third-party vendors to monitor, how much you want to monitor, when and for how long - that way you can have visibility into administrative activities and still respect employee privacy requirements as needed.
Detect and Prevent Threats Early and Automatically
Another crucial benefit of using StaffCop is that it allows you to identify high risks behaviors by insiders such as copying files to external drives, using cloud storage to share corporate files, downloading/opening files and attachments from unknown sources etc. In other words, the software automatically detects when employees violate the rules or act outside the normal behavior. It notifies companies of their employee’s activities, locks offending employees out from the system or takes remote control of their computer.

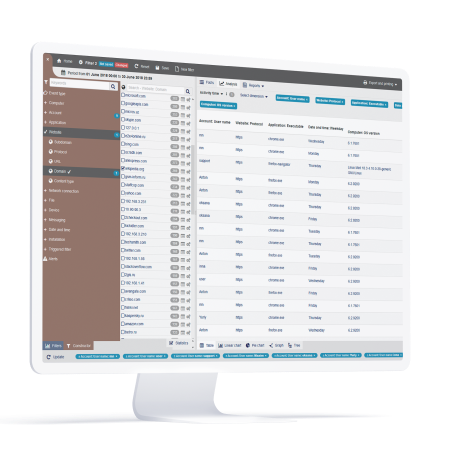
Protect Information and Resources with Data Loss Prevention Features
StaffCop’s rules react to any observable user activity like when certain sensitive document gets printed or any specific search query gets input, etc. It also asked you to tag sensitive files and specify who has access to them and which applications can be used to work with them. All these features are crucial in minimizing information exfiltration and data leaks.
Investigate Threat Incidents and Conduct Forensic Analysis and Audit
StaffCop is like a time machine. Thanks to its session recordings and history playback features, you can go back in time and see what a particular employee was doing in a specified period in the past, view breach events and actions that were taken in response to the incidents. Basically, these features help in auditing and evidence gathering.
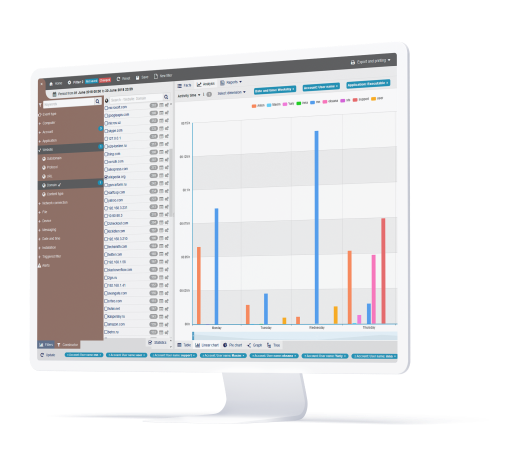
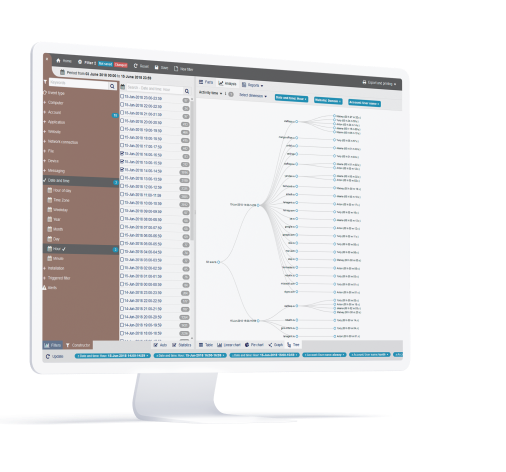
Monitor Privileged Users, Remote Users and Third-Parties to Prevent Collusion
StaffCop enables organizations to stop potential employee-employee or employee-third party collusion attempts: You can create profiles for remote, privileged, external vendors and define what information and system resources each profile can access using StaffCop. And use rules to set up by behavior policies so that access to sensitive information is separated by the organization’s security policy.
Reduce Risk Exposure and Protect Yourself with Proof
StaffCop determines what behaviors are high risk – using cloud storage to share corporate documents, copying files to external drives, downloading/opening files and attachments from unknown sources etc. Applies advanced behavior-based rules to automatically detect when employees violate the rules. And leverages sophisticated anomaly rules to identify employee activity outside the normal behavior.
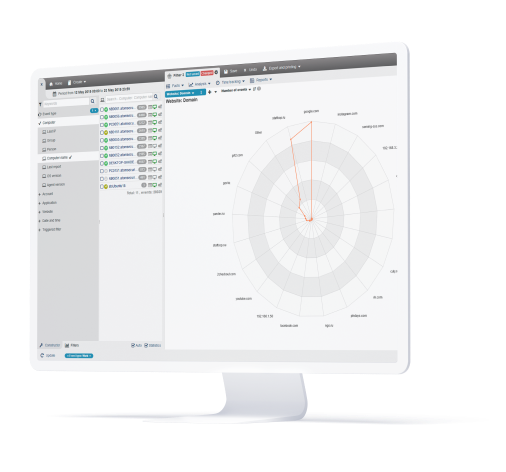

Block access to websites
You can use StaffCop to block particular web-sites that can be distracting or harmful for working process.
Black list. Add domains or URLs of web-sites that will be blocked. All other web-sites can still be accessed.
White list. Add domains or URLs of web-sites that will be allowed. In this example, we allowed access to StaffCop.com, Bitrix24 and Capterra. ALL other web-sites will be bloked. White lists are useful in case corporate policy allows working ONLY with a narrow range of web-sites.
Black list. Add domains or URLs of web-sites that will be blocked. All other web-sites can still be accessed.
White list. Add domains or URLs of web-sites that will be allowed. In this example, we allowed access to StaffCop.com, Bitrix24 and Capterra. ALL other web-sites will be bloked. White lists are useful in case corporate policy allows working ONLY with a narrow range of web-sites.
Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest. .
.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states..
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results..
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more.
630090, Novosibirsk, Kutateladze st., bl. 4G, Russia



